We’ve all been there, you receive an email from Microsoft, Dropbox, Google, maybe even your Bank institution asking you to reset or check your account settings. You look at the email, mull it over for a few seconds and then determine…. it looks legit, feels somewhat legit, must be legit!
You slowly move the cursor to the link provided in the email, you have second thoughts, quick flashes of past security training go through your mind but none of it applies to this email, so you click the link!
See, it is legit, the site is a Microsoft, Dropbox, Bank <fill in your own institution here> and it’s definitely legit, right? Still hesitant you fill in the fields and hit submit, but then a dreadful feeling comes over you and you realize, this is NOT LEGIT!
Moments like this can be avoided, with a few simple pointers.
Recently we received an email with the following message:
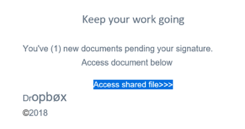
From the get-go, it did not look legit, at least we never remember Dropbox being spelled with a “Ø”!
However, understanding if an email is legit or not is relatively quick and easy, the individuals or entities that send these emails hope that you never figure out how to do just that because they know that when that happens there is no chance anyone will ever click the link.
The goal of these types of emails is to ultimately get you to click that link and enter your username and password by gaining your trust through a simple visual style. If it looks legit, sounds legit, then it must be legit. That’s not always the case, here are some easy ways to identify an email that is not legit.
- Organization Name in the Email. Is the organization name spelled exactly how it should be? In the example above, most people know how “Dropbox” is spelled, not with a “Ø” or bolded “opbØx”.
- Hovering the cursor over the link usually reveals the true link URL:
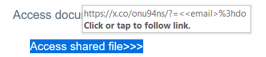
If this link does not match the organizations true to life domain name, guaranteed it is not legit.
- Clicking on the link causes the browser to display the following (the message may be different depending on the browser in use, the following message is displayed in Microsoft Edge):
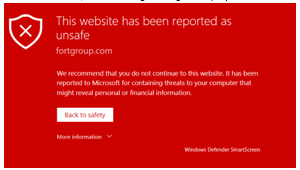
If the browser does not display the above message and goes to a legitimate looking site, check the browser address bar. The address listed will reveal whether the site is legitimate or not. Organizations like Microsoft, Dropbox, Google, Apple, and so many more have specific domain names they use. For example, Microsoft.com, dropbox.com, apple.com, these domain names do not deviate.
However, similar looking domains are created in order to fool the individual. For example, Apple’s popular iCloud domain name has been mimicked with names that match the first part but includes other characters, such as icloudhh.com.
Receiving an email where the URL looks like it has a legitimate domain name can be a little more troublesome to detect, but still not impossible. Preventing your confidential information from being compromised starts with awareness. Having these simple methods to identify an illegitimate request in your pocket will help to exploit a phishing scheme without falling victim to it.

Even worse is when someone you know, be it a personal or work relationship, falls victim to a phishing email. Their inbox is then used to spam their address book with further emails, utilizing the owners own signature. People tend to fall for these much more readily.
Excellent point. I plan on making an edit to this article to add such information.
Thanks for the Input!